Are you Familiar with these IT Security Concerns?
In today's digital landscape, it is a constant challenge to maintain an overview and stay one step ahead of attackers.
Hidden Vulnerabilities
You are asking yourself what undiscovered security vulnerabilities are lurking in your systems and could be exploited by attackers at any time.
Growing Compliance Requirements
The pressure to comply with regulations such as DORA, NIS2 and GDPR is increasing. Failure to do so can result in expensive penalties and damage to reputation.
Protecting the Value of your Business
A successful cyberattack not only damages your finances, but also destroys the hard-earned trust of your customers and partners.
Your Strategic Gain through Cooperation
Tangible Risk Minimisation
Proactively protect yourself against financial losses, business interruptions and reputational damage caused by cyber attacks.
Verifiable Compliance
Effortlessly meet the requirements of standards such as GDPR, TISAX or ISO 27001 and demonstrate your duty of care to partners and customers.
Clear Basis for Decision-Making
Unsere Berichte übersetzen komplexe technische Befunde in verständliche, priorisierte Handlungsempfehlungen für Ihr Management und Ihre IT.
Increased Trust & Competitive Advantage
Show customers, investors and partners that security is your top priority and set yourself apart from your competitors.
Our Analysis Methodology in Detail
Our penetration tests go beyond automated scans. We combine state-of-the-art tools with the creativity and experience of our IT security consultants to test your systems as a real attacker would.
Web Application Penetration Tests
For Web, SaaS, and Portals
Your web applications are often the primary target of attackers. We conduct an in-depth vulnerability analysis or security audit of your online shops, customer portals, or SaaS platforms to close critical gaps.
- Assessment according to OWASP Top 10 and beyond
- Analysis of business logic for design flaws
- Security checks for authentication and session management
- Detection of injection attacks (SQL, XSS, etc.)


Network Penetration Tests
The foundation of your Infrastructure
We analyze your IT infrastructure both externally (external tests) and internally (internal tests) to uncover misconfigurations, outdated services, and insecure protocols that could pave the way for attackers.
- Identification of open ports and vulnerable services
- Testing firewalls and segmentation concepts
- Analysis of Active Directory and internal systems
- Uncovering ways to escalate privileges
API and Mobile App Security
The Modern Attack Surface
Mobile apps and the APIs behind them are an often overlooked but critical gateway. With a security audit, we test the security of your mobile applications and all API communication.
- Assessment based on OWASP Mobile and API Security Top 10
- Analysis of data storage on the end device
- Security checks for the entire API endpoint logic
- Uncovering insecure authentication mechanisms

Our work is based on recognised standards
Process
What does a penetration test with Lutra Security look like?
- Initial consultation During an initial consultation, we will discuss your specific or less specific problem. We will first clarify how we can help you and whether you need us at all.
- Effort estimation
After the initial consultation, you will present the system in a scoping meeting. The underlying technology and technical basis will be explained in order to enable a well-founded cost estimate.
We will then send you a quote with our cost estimate.
- Kickoff
During the kick-off meeting, the tester’s final questions about the system are answered.
In addition, the tester’s requirements for conducting the assessment as efficiently as possible are discussed. In the case of a web application assessment, this could include various user accounts and firewall activation, for example.
- Assessment Generally, you do not need to participate during the actual assessment. However, a contact person should be available to answer specific questions from the tester.
- Reporting Each of our services includes a detailed report that describes the vulnerabilities and misconfigurations found in detail and provides specific recommendations for action.
- Debriefing & remediation
Of course, we won’t leave you in the dust after our service. We always offer a free follow-up meeting for our services, where we can chat about the results and answer any questions you might have.
And, of course, we’ll still be there for you afterwards and happy to answer any questions you might have.
More than just data: A report that adds value
A penetration test is only as good as its results. Many providers simply deliver a data dump – a long, incomprehensible list of findings. We believe that a report must empower you to take action. That’s why we translate technical data into clear insights and create a document that adds value at every level of your organisation: from management to the development department.
Management Summary
For management-level decisions, you don’t need technical details, but rather an assessment of the actual business risk. Our management summary is your one-page roadmap for strategic security decisions.
- Comprehensible risk assessment: We summarise the general security situation in clear, non-technical terms.
- Business impact analysis: We highlight the potential impact of the vulnerabilities found on your business processes, reputation and finances.
- Top strategic recommendations: You will receive the 2-3 most important strategic measures that will lead to a significant improvement in your security.

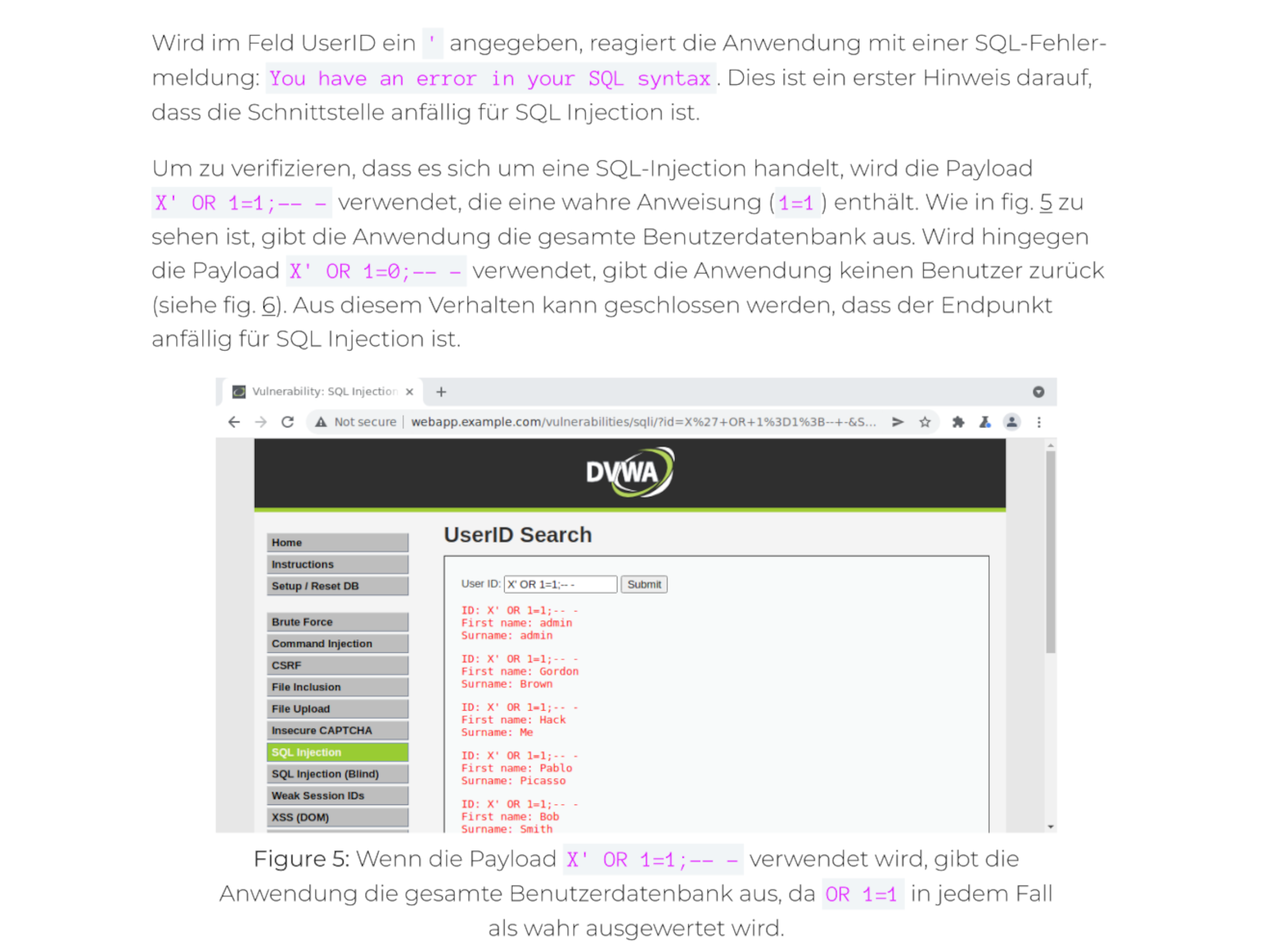
Technical Analysis: Precise Findings for your IT Team
Your technical experts need accurate, reproducible information to efficiently fix vulnerabilities. Our technical section is designed precisely for this purpose.
- Detailed description of vulnerabilities: Each identified vulnerability is described along with its cause and impact.
- Reproducible steps (proof of concept): We document the exact steps and provide the necessary evidence (e.g. screenshots, code snippets) so that your team can understand the vulnerability without having to spend a long time searching for it.
- Attack scenario: We show how individual, seemingly harmless vulnerabilities in a chain can be exploited to cause maximum damage.
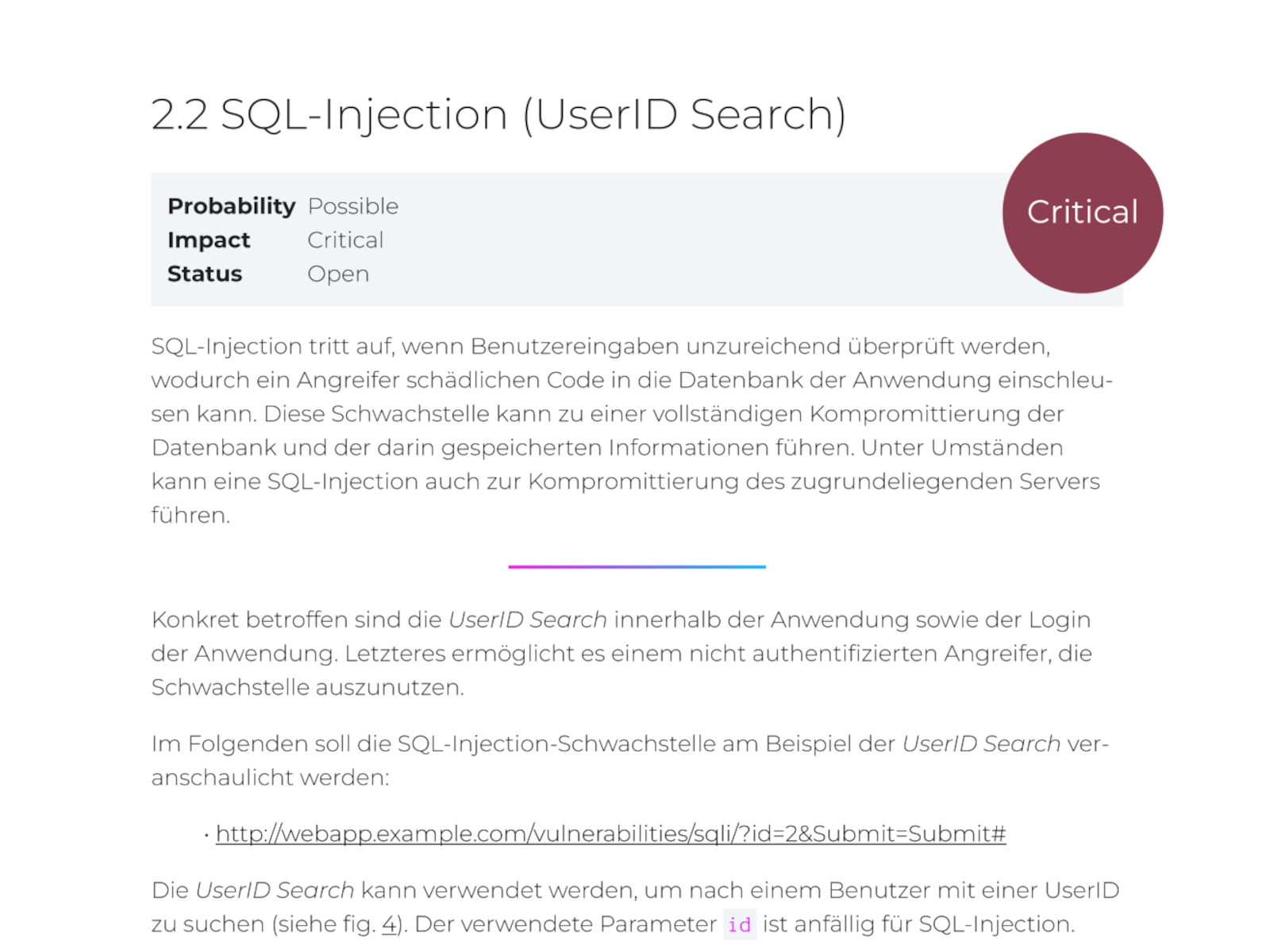
Risk assessment & prioritisation: Targeted use of resources
Not all vulnerabilities are the same. To make the best use of your budget and time, we evaluate each finding according to industry standards such as the CVSS (Common Vulnerability Scoring System).
- Clear risk categories: Each vulnerability is assigned one of four levels of overall risk: Critical, High, Moderate or Low.
- Transparent rating: The rating is based on factors such as the complexity of the attack, the level of authorisation required and the potential damage to the confidentiality, integrity and availability of your data.
- Your advantage: You invest your resources exactly where they are most urgently needed and first address the vulnerabilities that pose the greatest risk to your business.
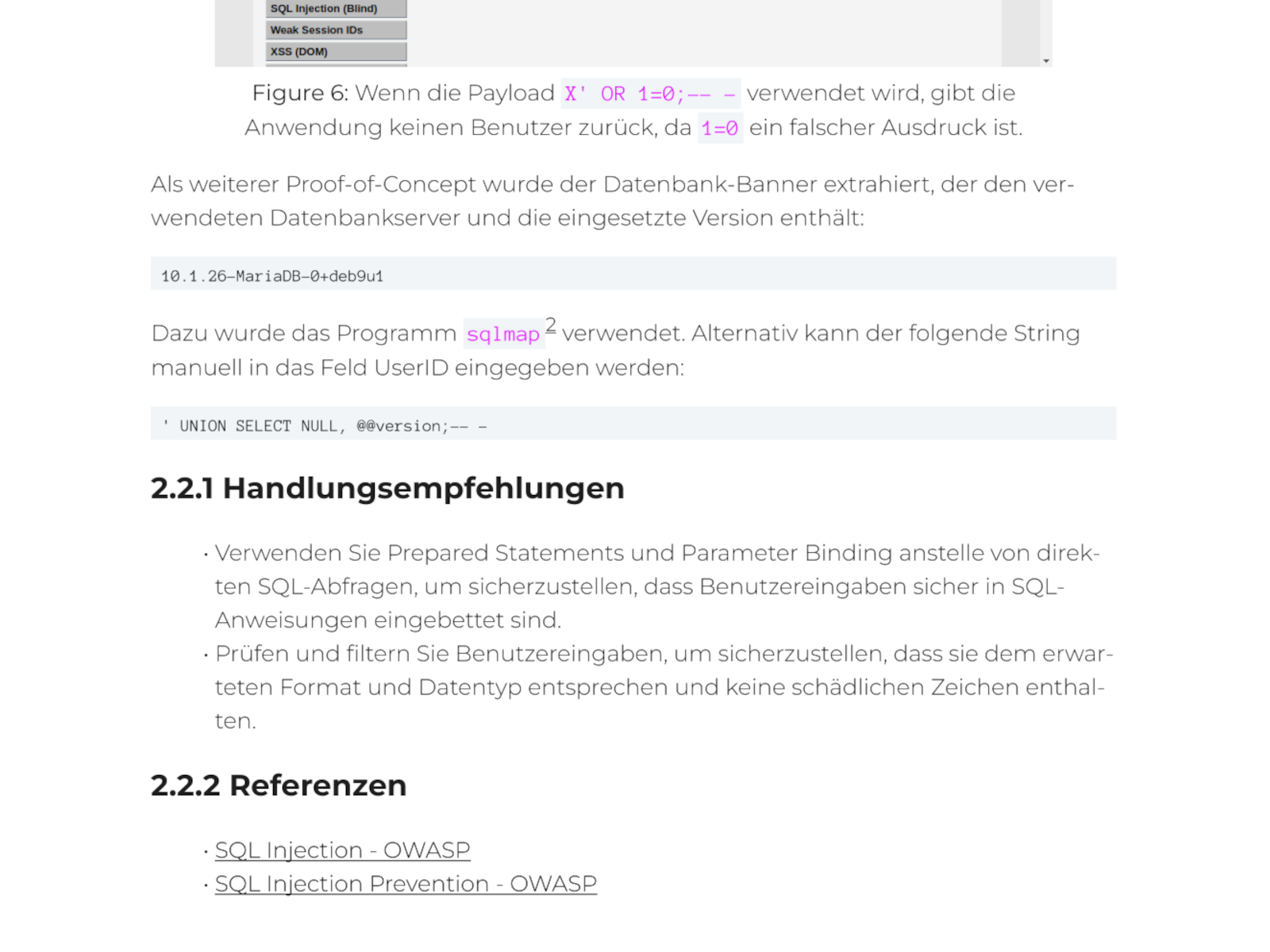
Practical recommendations: From knowledge to action
We won’t leave you alone with your problems. For every vulnerability identified, we provide clear and actionable instructions for remediation.
- Practical solutions: Instead of simply referring to external guidelines, we provide specific recommendations tailored to your technology and architecture.
- Examples & references: Wherever possible, we back up our recommendations with code examples, configuration suggestions and links to official manufacturer documentation.
- Root cause analysis: We not only help you fix the symptom, but also understand the underlying cause to avoid similar mistakes in the future.
See for Yourself: Request our Sample Report
Convince yourself of the quality and clarity of our work. Request our sample report now and also receive access to our newsletter with regular insights into IT security.
Our areas of expertise in penetration testing
On-site penetration test
Working face-to-face to hunt down vulnerabilities and uncover security issues. Whether you need consulting, penetration testing or code review, we are happy to visit you and provide personalised services on site.
Learn moreAPI penetration test
APIs, whether REST, GraphQL or SOAP, are simply part and parcel of a digitalised world. Identify vulnerabilities now, before real attackers do. The essential security check for your application interfaces.
Learn moreWeb penetration test
Web applications have become an integral part of our everyday lives. Whether it’s an external SaaS solution or your own software product, we systematically identify vulnerabilities in your web applications before attackers do.
Learn moreRed Teaming
Are you and your company ready for the ultimate test of red teaming? We slip into the role of real attackers and use all the techniques and tricks from MITRE ATT&CK. Can you detect and stop us? The reality check for your company.
Learn moreReady to put your defence to the test?
Contact us for a free, no-obligation initial consultation, during which we will analyse your requirements:
Founded by experts. Driven by your safety.
We are not an anonymous agency. Lutra Security was founded by four IT security experts with a shared mission: to proactively protect companies and make complex security solutions understandable and accessible. Your security is personally guaranteed by the founders.

David Schneider

Emanuel Böse

Konstantin Weddige
